2018 Verizon DBIR
The 2018 Verizon Data Breach Investigations Report (DBIR) is here! I may sound like a total fanboy – but I am. I will try to pull out a few good examples for you, but I highly recommend getting yourself a full copy.
Download the full report here.
Each year there is a ton of good information contained in the DBIR. For example:
This year we have over 53,000 incidents and 2,216 confirmed data breaches.
Where else are you seeing that population size to identify common themes and trends?
One of the interesting summary graphics presented in the report was the source of breaches:

28 percent?! That is a significant portion of attacks being perpetrated by internal users – is your organization in a position to detect this malicious insider? With this level of involvement I would say you can’t afford not to.

The important statistic here is the detection rate – we are still not detecting incidents in a timely manner! The report goes on:

In addition to the AWESOME report, Verizon has also released an Insight tool for you to interact with the data. Head on over here to check it out.
But wait… There’s more!
2018 M-Trends Report
Mandiant (FireEye) puts out a similar style report “M-Trends2018”. You can grab a copy here. Looking at the glass half full – things improved this past year!
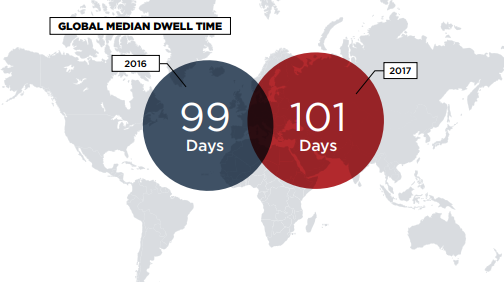
The M-Trends report has a pretty interesting section looking into repeat attacks against organizations. Once a company has been attacked, 38% of those companies were attacked again. Many of these attacks were attributed to the same, or a related, group.
The M-Trends report also calls out the risks at the endpoints – implementing controls to prevent and detect the impact of phishing against end users. Controls like application whitelisting and detailed monitoring of activity were mentioned.
Defenders have to get it right every single time, while threat actors only need to get it right once.
2018 Cybersecurity Almanac
This report is the first of it’s kind from Momentum Cyber. You can download the full report here. The few excerpts I included below are just starting to form the tip of the iceberg of information contained within the report.
In true Almanac fashion, the report provides an overview of the last year, with significant events/dates laid out. There is also a good amount of statistical data, covering both the last year in breaches and investment activity – as well as predictions for trends in the coming year.


There is an incredible amount of information surrounding M&A activity an analysis, something that is certainly interesting to keep an eye on – especially with so many organization’s using third parties to cover the “InfoSec Skills Gap”. Are any of the vendors you are working with looking to be acquired? Have you considered this in your strategic planning?

Momentum Cyber focuses on M&A as their main business – in their own words:
Momentum Cyber provides world-class M&A and strategic advice combined with unparalleled senior-level access to the Cybersecurity ecosystem. We advise on a broad range of strategic activities, including mergers and acquisitions, board & special situations, corporate strategy & development, corporate finance, and operational excellence. We are a mission driven firm with a passion for Cybersecurity.